Network infrastructure planning and design is a vital component of any successful enterprise. It requires careful thought, consideration, and implementation to ensure that all aspects of the network are running efficiently and securely.
This article will explore best practices and considerations when it comes to network infrastructure planning and design, guiding how to create an effective system for your organization.
From taking inventory of existing hardware to mapping out future growth plans, this article will provide insight into building a stable foundation for your business data needs.
Additionally, tips on selecting the right vendors and designing optimal networks for scalability will also be discussed to make sure that you can maximize efficiency within your system while still meeting regulatory requirements.
With the right knowledge at hand, you can confidently move forward with creating a reliable network architecture tailored specifically to each organization’s unique needs.
1. Establishing Infrastructure Requirements

When designing a network infrastructure, one of the most important steps is to establish and identify the right requirements. An organization must thoroughly understand its current needs and plan for future growth to ensure that the chosen solution meets all its technical, operational, and financial goals.
In addition, it is essential to carefully consider existing resources such as hardware availability, personnel experience levels, scalability options, and other relevant factors. The goal should be to determine what type of infrastructure components are necessary for successful implementation while also considering how they integrate with existing systems if applicable.
Additionally, organizations must take into account any potential risks associated with implementing new technology or expanding an existing system before making decisions about design elements like topology selection or bandwidth provisioning.
Taking these considerations into account will help create a solid foundation for any network infrastructure project that can accommodate changes over time without compromising performance or security objectives.
2. Planning Network Topology and Architecture
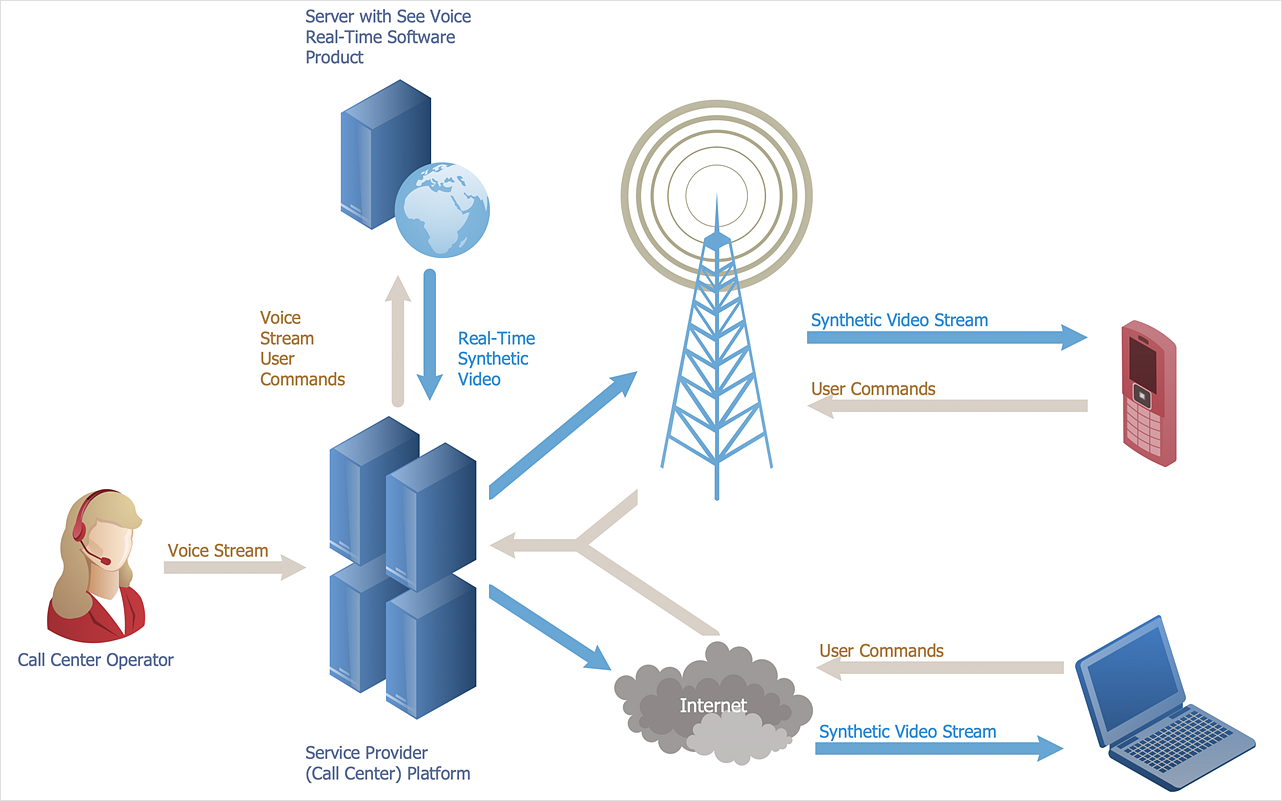
When planning network topology and architecture, it is important to consider the scope of your infrastructure. Depending on the size and complexity of your network, you may need to use different methods for designing an optimal solution. For smaller networks with fewer users, a simple star-shaped topology may be sufficient for basic connectivity needs.
However, if more complex applications are being used in larger networks with multiple nodes, then a mesh or ring topology might be necessary.
Additionally, when creating the architecture of a network it is essential to ensure that all components such as routers and switches are properly configured so that they can communicate effectively with each other without any service disruption.
It is also important to have adequate redundancy measures in place so that should one device fail there will still be reliable connections between nodes within the system. Furthermore, security protocols must be implemented which support authentication and encryption standards appropriate for data integrity within the system.
Ultimately this means ensuring secure access control practices across all devices connected to the network while maintaining performance throughputs suitable for user requirements at every layer of communication within the system
3. Implementing and Monitoring Performance

Once you have identified the best network infrastructure plan for your business, the next step is to begin implementing and monitoring it. Taking a systematic approach to this process is key to ensuring that everything runs smoothly and efficiently while preventing any potential problems down the line.
The first step in implementation involves evaluating all of the hardware that will be used within your system. Make sure each piece meets industry standards and has enough capacity for current needs and future growth projections.
Also test components ahead of time such as routers, switches, firewalls, etc., so there are no surprises when they are installed into production environments. Additionally, review existing protocols from third-party vendors before making changes or additions to ensure compatibility with new hardware or software upgrades.
Once all of these steps have been completed successfully you can then move on to installing your network components in their designated locations according to plan specifications.
For this part of the process to go smoothly all personnel involved must understand their roles and responsibilities during installation as well as how they work together toward achieving a common goal – successful completion of set tasks on schedule without disruption in service or security breaches.
Finally, once these pieces are up and running you’ll need someone responsible for regularly monitoring performance metrics such as uptime percentage, latency figures by connection type (LAN vs WAN), security breach attempts/failures per day/week/month, etc., which help indicate whether adjustments need to be made or if additional resources should be allocated elsewhere within the infrastructure itself over time-based on usage patterns observed through network traffic analysis reports generated at regular intervals throughout its lifecycle – continuously optimizing various aspects makes certain systems remain secure & reliable over extended periods without compromising user experience due its responsiveness under heavy loads & changing conditions at any given moment
Conclusion

In conclusion, network infrastructure planning and design require careful consideration of several best practices. It is important to remember that while technology can be a powerful tool in achieving an efficient, reliable, and secure network, it must also be tailored to the specific needs of the organization.
Additionally, when writing content for the organization’s website or other documents related to its network infrastructure it is crucial to keep both perplexity and burstiness in mind for the text to read naturally.
By taking into account these considerations when creating any type of communication about a company’s networking environment, organizations will ensure their message is understood clearly by all stakeholders.


